Ensuring Video Conferencing Security: Risks, and Best Practices
In the rapidly evolving digital business landscape, effective communication across borders plays a vital role in achieving success. When it comes to video communication, video conferencing becomes the best choice for businesses to communicate. As such, prioritising security for your video conferencing platform or services is crucial.
Table of contents
- Understanding video conferencing security risks
- Key factors in video conferencing security
- Privacy best practices for video conferencing
- GDPR compliance in video conferencing
- Reviewing the best video chat software for PC security
- Digital Samba's commitment to providing secure video conferencing solutions
In this article, we are going to explore the world of video conferencing security as we explore best practices, potential risks, compliance obligations, and secure solutions
Understanding video conferencing security risks
When it comes to video conferencing, most conference participants do not consider the security issues that may be present in a conference call. Although some of the vulnerabilities might seem quite obvious, let’s have a look at some of the most common vulnerabilities:
Unsecured endpoints
Malware and phishing attacks
Participants may unknowingly download malware-infected files or fall victim to phishing attempts during conferences.
Unencrypted connections
Lack of security updates
Eavesdropping
Intellectual property theft
Data leakage
Impersonation attacks
Key factors in video conferencing security
Robust encryption techniques
In the realm of video conferencing security, robust encryption techniques play a vital role in safeguarding sensitive information and maintaining the confidentiality of communications.
- Explaining the importance of encrypted video conferencing through E2EE
End-to-end encryption is a crucial security measure that ensures only the intended recipients can access and decipher the transmitted data. With E2EE, the data is encrypted on the sender's device and can only be decrypted by authorised recipients. This means that even if the communication is intercepted, the encrypted data remains incomprehensible and protected from unauthorised access.
- Ensuring secure web conferencing communication and data protection
Implementing secure communication protocols, such as Transport Layer Security (TLS) and Secure Real-Time Transport Protocol (SRTP), adds an extra layer of protection to video conferences. These protocols establish secure connections and encrypt the data transferred between participants, preventing unauthorised interception and tampering. Additionally, employing encryption for stored data on servers enhances data protection even when not actively in transit.
Authentication and access controls
Authentication mechanisms and access controls are crucial aspects of video conferencing security, ensuring that only authorised individuals can participate in meetings and access sensitive information.
- Implementing strong user authentication mechanisms
Robust user authentication mechanisms, such as two-factor authentication (2FA) and biometric authentication, add an extra layer of security by requiring users to provide multiple forms of identification. This mitigates the risk of unauthorised access through stolen or compromised credentials and strengthens overall system security.
Keep Your Virtual Meetings Secure with Token Authentication
Read the blog
- Role-based access controls for secure video sessions, meetings and data sharing
Role-based access controls (RBAC) allow administrators to assign specific roles and permissions to participants by enforcing the principle of least privilege. This minimises the risk of data breaches or unauthorised data disclosure.
RBAC allows organisations to assign users access and authorisation to specific actions or data depending on their role. For instance, an admin may have access to all the confidential data shared within a video conference. While a participant may be allowed to take part in the call and be restricted from accessing any shared files.
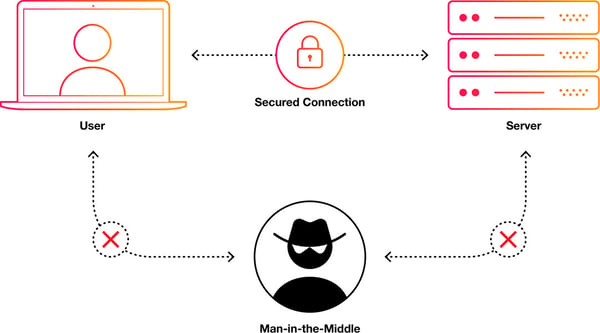
Video conferencing security best practices
Minimising personal data exposure
To protect participants' privacy in video conferencing, it's essential to adopt practices that minimise the exposure of personal data.
- Collecting only essential personal information
When setting up video conferencing platforms, it's crucial to collect and store only the necessary personal information required for identification and authentication purposes. Avoid requesting excessive details that are unrelated to the purpose of the meeting. By minimising the collection of personal data, the risk of unauthorised access and potential data breaches can be reduced.
- Anonymising and pseudonymising user data
To provide an additional layer of privacy, consider anonymising or pseudonymising user data whenever possible. Anonymisation involves removing personally identifiable information, while pseudonymisation replaces identifiable data with artificial identifiers.
By doing so, you protect your participants’ data and enforce data privacy making it more difficult for unauthorised users to link data to a specific user.
Transparent privacy policies
Clear and transparent privacy policies are vital in establishing trust and ensuring participants understand how their data is handled during video conferences.
- Communicating Cpclear privacy policies to users
Video conferencing providers should communicate their privacy policies to users in a clear and easily accessible manner. Participants should be informed about the type of data collected, the purposes for which it is used, and any third parties with whom the data may be shared.
This transparency enables users to make informed decisions about their participation and assess the level of privacy protection offered.
- Providing information on data handling and retention practices
Privacy policies should also include information about how data is handled and retained. This includes details about the security measures in place, data storage locations, data center sustainability for server uptime, and the duration for which data is retained.
By doing so, organisations assure their participants that their data is being managed securely and responsibly. This also allows users to consider the associated risks and mitigation measures.
GDPR compliance in video conferencing
Understanding the General Data Protection Regulation
The General Data Protection Regulation (GDPR) is a comprehensive privacy regulation implemented in the European Union (EU) to protect the rights and privacy of individuals. It establishes strict guidelines for the collection, processing, and storage of personal data.
Ensuring video conferencing platforms are GDPR-compliant
Video conferencing platforms must adhere to GDPR requirements to ensure the protection and safety of personal data during meetings.
GDPR Compliance in Video Meetings: What You Need To Know
Read the blog
To achieve GDPR compliance, platforms should implement measures such as:
Lawful basis for data processing
Data subject rights
Data protection impact assessments
Data breach notifications
Reviewing the best video chat software for PC security
When choosing a video conferencing software that focuses on PC security, it’s important to go through its security features and ensure it matches your security and data privacy requirements. While there are hundreds of video chat software, here are some top picks that focus on security:
- Digital Samba: Known for its focus on security and privacy, Digital Samba offers advanced encryption, authentication mechanisms, and data protection features.
- Microsoft Teams: relies on E2EE to protect videos or chats from being intercepted and mandates 2FA for enhanced security and sign-on options.
- Skype: uses E2EE to protect voice and video calls, deploys a private profile ID only available to authorised users and proprietary encryption algorithms for secure chats.
Digital Samba's commitment to providing secure video conferencing solutions
When considering a secure video chat platform, integrating a VaaS like Digital Samba can significantly transform your business. Digital Samba is committed to delivering secure video conferencing solutions to ensure the privacy and confidentiality of your online meetings. With a strong focus on authentication & access control, security and data privacy, Digital Samba employs industry-leading encryption techniques to safeguard your communications.
FAQs
Video conferencing security varies by platform but generally includes encryption, access controls, and data protection measures to safeguard communications.
The most secure video conferencing platforms are those with end-to-end encryption, strong user authentication, and data privacy compliance (e.g., Digital Samba).
Secure Real-Time Transport Protocol (SRTP) is commonly used to secure video conferencing by providing encryption, message authentication, and integrity assurance for the media streams.
Ensure secure video conferencing by using platforms with end-to-end encryption, enabling strong passwords or meeting locks, and regularly updating software to protect against vulnerabilities.
A key security precaution is covering the video camera when not in use and ensuring that camera access is controlled and monitored to prevent unauthorised observation.
By choosing Digital Samba as your video conferencing provider, you can have confidence in the security of your virtual interactions with the most secure video conferencing platform.
Share this
You May Also Like
These Related Stories

GDPR Compliance in Video Meetings: What You Need To Know

Understanding WebRTC Security: Best Practices and Considerations